Pleased to have been a co-author for an upcoming Black Hat briefing on autonomous cyber defence.
Future cyber threats include high volumes of sophisticated machine speed cyber-attacks, able to evade and overwhelm traditional cyber defenders. In this talk, we summarise a large body of UK Defence research extending and applying Reinforcement Learning (RL) to automated cyber defence decision making, e.g. deciding at machine speed which action(s) to take when a cyber-attack is detected.
To support this work, we have matured simulators and tools including development of advanced adversaries to improve defender robustness. Promising concepts include two contrasting Multi Agent RL (MARL) approaches and deep RL combined with heterogenous Graph Neural Networks (GNNs).
Demonstration systems include Cyber First Aid, industrial control systems, and autonomous vehicles. We have demonstrated that autonomous cyber defence is feasible on 'real' representative networks and plan to increase the number of high-fidelity projects in the next year.
 I had the pleasure of talking about how we're using co-evolutionary reinforcement learning to simulate defenders and adversaries in computer networks on the Spotlight Stage of Cyber UK this year.
I had the pleasure of talking about how we're using co-evolutionary reinforcement learning to simulate defenders and adversaries in computer networks on the Spotlight Stage of Cyber UK this year.
As always, it was a great event, always good to catch up with those looking at national scale cyber defence as well as all the amazing solutions that are emerging.
A lot of discussion focussed on the changing nation state threat landscape and victim profiles. Perhaps the more interesting topics though were those that feel like they're shifting from being fringe to much more mainstream - PUFs, quantum and synthetic computational biology.
My personal highlight was receiving some Glencairns as a consolation prize for coming close to winning a lockpicking challenge. Crowdstrike also did not disappoint with their APT themed t-shirts as usual.

Geoff White did a highly engaging talk on the Lazarus Heist. It was also interesting to hear from the British Library, on their response to the recent cyber attack - something a think a lot of organisations can use as an example.

Some fantastic work driven by two researchers from my team, presented earlier this month at the 43rd BCS SGAI conference - the UK's longest running AI conference. Aptly named for the season.
With the exponential increase in devices connected to the Internet, the risk of security breaches has in turn led to an increase in traction for machine learning based intrusion detection systems. These systems involve either supervised classifiers to detect known threats or unsupervised techniques to separate anomalies from normal data. Supervised learning enables accurate detection of known attack behaviours but requiring quality ground-truth data, it is ineffective against new emerging threats.
Unsupervised learning-based systems address this issue due to their generalizable approach; however, they can result in a high false detection rate and are generally unable to detect specific types of each threat. We propose an ensemble technique that addresses the shortcomings of both approaches through a semi-supervised approach which detects both known and unknown threats in the network by analysing traffic metadata.
The robust approach integrates A) an adversarial regularisation based autoencoder for unsupervised representation learning and B) supervised gradient boosted trees to detect the type of detected threats. The adversarial regularisation enables a reduced false positive rate and the combination of the autoencoder with the supervised stage enables resiliency against class imbalance and caters to the ever-evolving threat landscape by detecting previously unseen threats and anomalies.
SANTA’s ability to detect never-before-seen threats also indicates its potential to address the concept drift, a phenomenon where the known threat changes its behaviour/attack sequence over time. The system is evaluated on the CSE-CIC-IDS2018 dataset, and the results confirm the resilience and adaptability of the SANTA system against known shortcomings of both supervised and unsupervised approaches.
Image from Microsoft's DALL-E.
Whilst we have used a handful of SM platforms as illustrative examples, we have argued that, broadly, these data collection routes and the Terms that govern their use pose substantial restrictions that not only threaten the transparency of our research but, more fundamentally, risk restricting the advancement of our knowledge on human behaviour.
Over the past few years, there's been a pressing need for increased understanding of the role dis/misinformation plays in society.
One of the problems is the high accessibility of misinformation in social media. You would expect this to be a boon to researchers, but on the contrary, complex terms of use and limitations in API are problematic for data collection.
Earlier this year, I had the chance to collaborate with a fantastic group of researchers on a comment for Nature Human Behaviour in an effort to raise awareness of the issue.
Absolutely fantastic news from the recent E&T Awards. E&T is magazine of the Institution of Engineering and Technology (IET's) and the annual awards, this year hosted by Dr Shini Somara celebrate ground-breaking innovations from the world of Science, Engineering, Technology and Maths (STEM).
Inflame, BT's epidemiological malware modelling tool won both the Innovation awards for Intelligent Systems and Cyber Security, as well as taking a silver prize for overall Innovation.
In the modern world, ransomware is a critical threat facing businesses and national infrastructure. Pedro Marques, Jonathan Roscoe, Dylan Jones and Luke Booth presented Inflame, a malware simulation and response tool that utilises epidemiological modelling and deep reinforcement learning to forecasts threats and help determine necessary defensive actions.
Inflame’s automated responses to cybersecurity threats are able to cut response times to a matter of seconds, easing the pressure on analysts and allowing experts to explore the potential effects of new threats, saving large amounts of money and preventing terrible damage. The tool has been deployed by Eagle-i, BT’s new security platform.
The judges considered that the application of epidemiological threat modelling and reinforcement learning to the fight against malware is “a significant innovation in an area where continual improvement is desperately needed to keep up with ever-evolving threats and to react faster to time-critical incidents”.

Excited to have a recent patent grant on improvements to DLT with quantum techniques.
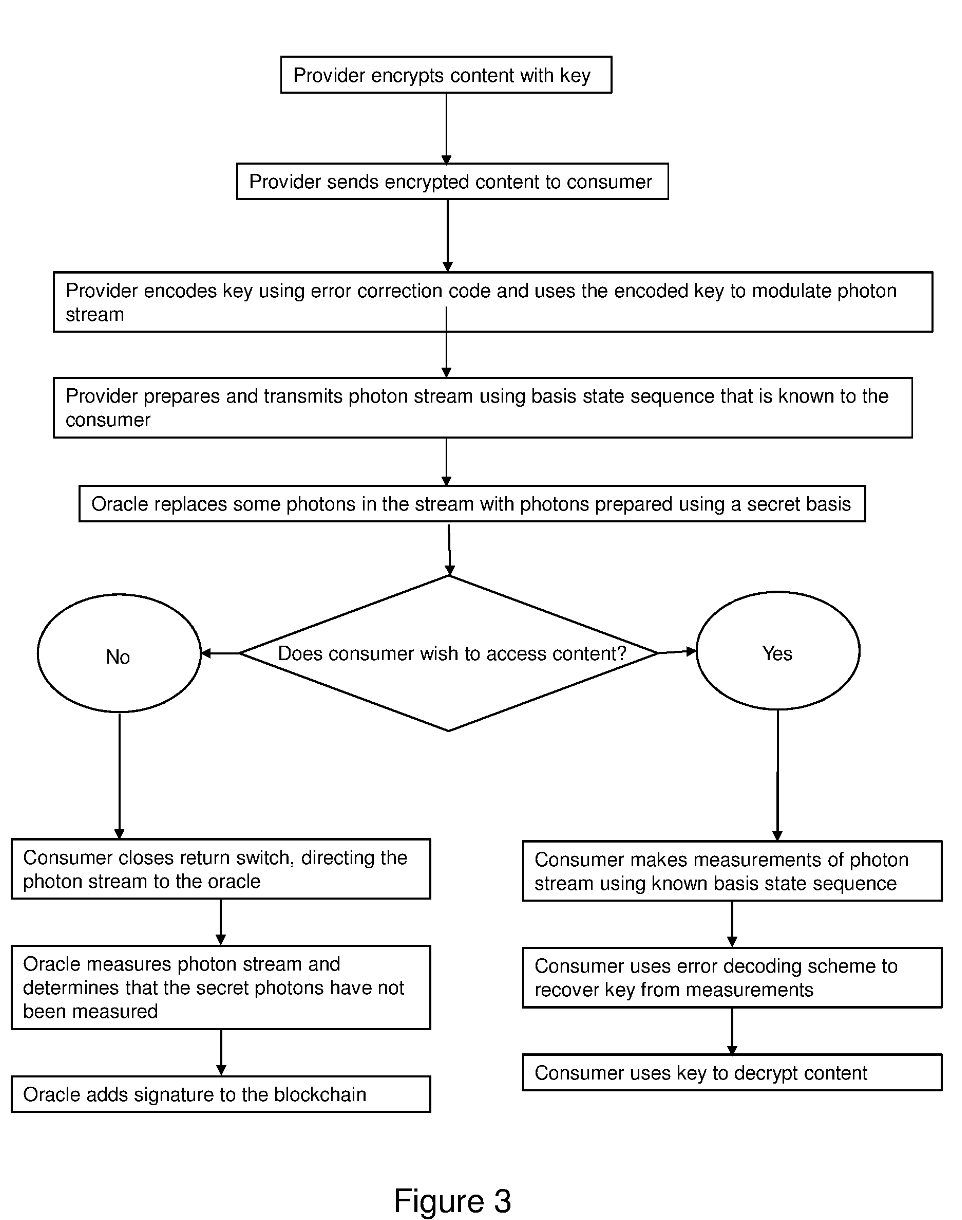
Distributed ledger (or blockchain) technology uses cryptographically signed chains of transactions to record the transfer of digital assets. In many implementations, these assets have a monetary value associated with them. There may be multiple types of assets on a blockchain, so for example a data asset may be transferred in exchange for some monetary value.
Distributed Ledger Technology enables “trustless” transactions thanks to the ability of all participants to validate transactions. However, in more complex transactions known as smart contracts, assets cannot always be adequately secured. For example, the delivery of digital assets as part of a transaction can be confirmed by the sender or the receiver, but this presents a byzantine problem, as it is difficult to prove that the receiver has received the digital assets.
Data on a blockchain is visible to all participants, though in some implementations side channels may be used to enable the exchange of information in secrecy. The participants in those side channels provide cryptographic hashes that summarise their transactions, without giving the details.
However, participants in those side channels may be misled or come to some disagreement with no facility for remediation. For example, in some situations, it is not clear whether a consumer has accessed the asset that is the subject of the transaction. It is therefore not clear whether the transaction should be added to the blockchain. The way around this is the use of third-parties providing escrow services, but that relies on trust in those third-parties. In particular, the third party asset may need to have a copy of valuable or confidential digital assets, which is not desirable.
It is desirable to overcome and/or mitigate some or all of the above-mentioned and/or other disadvantages associated with the prior art.
According to a first aspect of the invention there is provided a method of transmitting quantum-encrypted data from a quantum transmitting apparatus to a quantum receiving apparatus, the method comprising: indicating to a quantum receiving apparatus that a first sequence of mutually non-orthogonal bases will be used to prepare at least some of a plurality of bits in quantum states, at a quantum transmitting apparatus, preparing each of the plurality of bits in a respective one of a second sequence of mutually non-orthogonal bases, to give a plurality of qubits, wherein the second sequence of mutually non-orthogonal bases is different to the first sequence of mutually non-orthogonal bases.

Recently I was awarded Accomplished Engineer status within BT's Tech Fellowship, an internal community of technologists dedicated to influencing the technology landscape and supporting each other in advancing technology together.
I'm really passionate about continuing professional development. Personally, learning has always been a big part of my life and I'm motivated by new challenges and opportunities. It's great to be recognised as a substantial contributor to BT's technology output, I've worked with some excellent teams and individuals on exciting projects that have played a substatial role in my professional development.
For me, the Fellowship has been an opportunity to reflect on what I've accomplished during my time at BT and think about what I want my career to be in the future. Despite pressure and challenges both inside and out, I think BT has a lot of excellent opportunities and a huge role to play in the future of cyber security.
If you're interested in learning more about a role at BT, feel free to get in touch with BT.
I am absolutely thrilled to be exhibiting at CYBERUK22!
As co-lead sponsors of the event, BT is incredibly proud to support this amazing event that helps to bring the cybersecurity community together.

CYBERUK has become a key date in the calendar for thought leaders in cyber security and technical professionals from the UK and around the world, with previous conferences taking place in Liverpool (2017), Manchester (2018) and Glasgow (2019).
Building on the success of 2021’s virtual event, keynote speeches will also be streamed on the CYBERUK YouTube channel in order to maximise accessibility for all.
In "Acoustic Emanation of Haptics as a Side-Channel for Gesture-Typing Attacks" we demonstrated an update to the classical technique of analysing acoustic emanations from keyboards that applied to touchscreen typing now standard in mobile devices. Specifically, the technique applies to gesture typing and the acoustic emanation is from the haptic feedback motor, rather than from individual key presses.
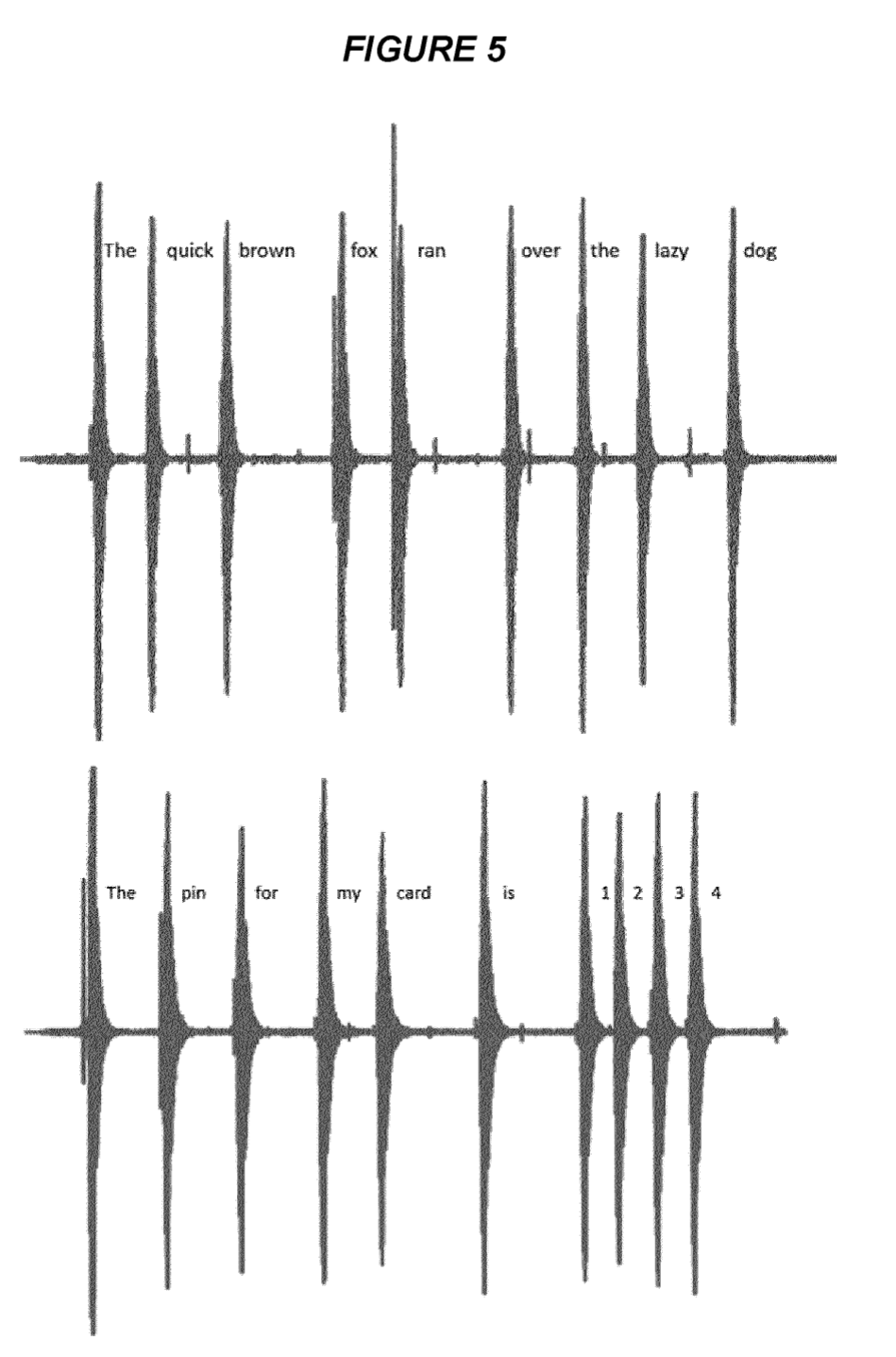
With a related patent, "Data Interception Protection" we propose modifications to input and feedback mechanisms to mitigate the risk associated with such an attack.
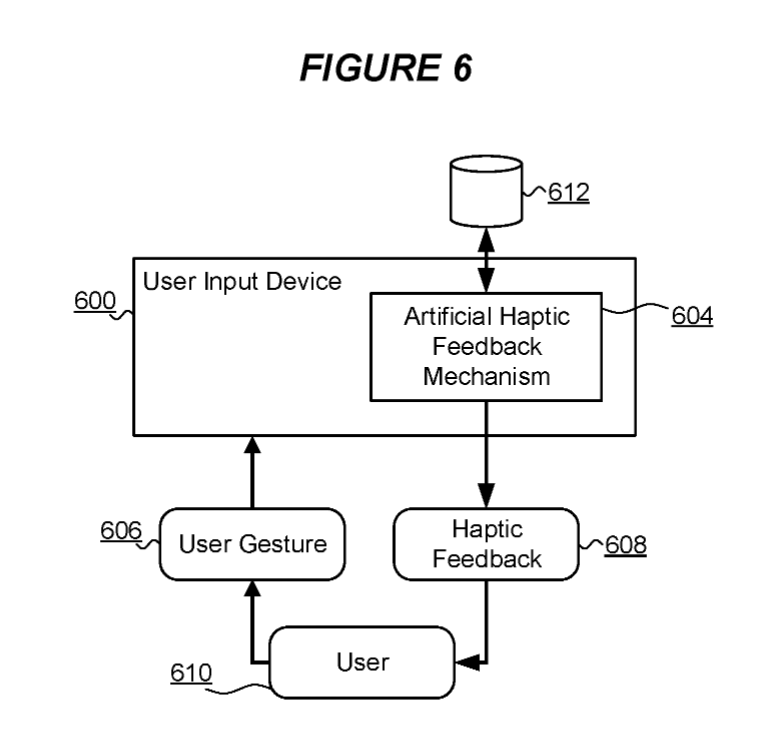
The main claim is as follows:
A computer implemented method to protect data input to a user input device from detection, the device including an artificial haptic feedback mechanism arranged to generate an occurrence of haptic feedback for sensing by a user of the device in response to each input gesture on the device by the user, characterised in that at least a subset of each occurrence of haptic feedback is adjusted with respect to a previous occurrence of haptic feedback by one or more of: a timing of the haptic feedback with respect to a time of occurrence of a corresponding input gesture; an adjustment to a duration of haptic feedback relative to a duration of the previous occurrence of haptic feedback; and a generation of one or more addition occurrences of haptic feedback.
 I'm still finding VQGAN+CLIP with the ImageNet model a really interesting tool for image synthesis. You can define an initial image, that is then iterated upon to match the prompt, for example, here's a picture of Adastral Park, iterated using the prompt "Cyberpunk".
I'm still finding VQGAN+CLIP with the ImageNet model a really interesting tool for image synthesis. You can define an initial image, that is then iterated upon to match the prompt, for example, here's a picture of Adastral Park, iterated using the prompt "Cyberpunk".

Or how about "fairy-tale castle"?

With a light touch you can change an image into another style, with a heavier touch you can create entirely new scenes that retain a reminisence of the original.
I can see this being highly applicable to games, but I also wonder if there's a potential opportunity in data visualisation. With the right weighting of prompts and using a combination of text and image, you could create consistent transformations that change how a user experiences data.
"An ancient tower looming above a city":

I've been developing a short Dungeons and Dragons campaign recently, as part of a first attempt at acting as a dungeon master.
I spent some time looking for reference images to use to set the scene and create an atmosphere for the story, but they are never quite what I'm looking for, though often they're good enough to paint a scene.
However, recently I came across Taming Transformers for High-Resolution Image Synthesis and the VQGAN+CLIP notebook by Katherine Crowson which is available for easy reuse as a python application.
GANs and various forms of image synthesis aren't particularly new, but a well packaged library for running them on a variety of high-quality models is. VQGAN is Vector-Quantized Generative Adversarial Network, a variation on the earlier VQVAE that aims to maintain higher perceptual quality. CLIP is Contrastive Language-Image Pre-training and is used to identify images based on natural language.
The VQGAN+CLIP scripts bundle these together, allowing you to define natural language prompts that are then used to generate synthetic images using VQGAN.
"Girl in long coat running down alley":

Using the Imagenet model you can generate some brilliant fantasy images that I feel make excellent prompts for the theatre of the mind - a term used to describe how RPG players must imagine the world in which their characters are in. This relies on descriptions by a GM, audio prompts and reference images. It's important to strike a balance, to provide just enough cues to let the player's imagination take over.
"A wizard looking at shelves of potions.":

I think the synthetic images are perfect for this. They don't prescribe too specific scene as they lack detail but they have enough information to act as recognisable prompts.
"A purple haired girl riding a dragon":

The use of prompts such as "surreal", "CGI", "unreal engine" and colour palettes can be a great way to build a collection of images with a consistent theme. For example, the same prompt with different keywords as secondary prompts (0.75 weighting):
"A wizard stands before a dragon | sketch":

"A wizard stands before a dragon | unreal":

"A wizard stands before a dragon | photorealistic":

"A wizard stands before a dragon | blueprint":

You can even weight and chain multiple prompts so that certain elements become more prominent, allowing you a large degree of customisation.
Results can vary a lot and it can take some work to find the prompts that produce a satisfying image. The work is also computationally expensive, my RTX 2080 with 8GB VRAM can only produce 380x380 images and each takes about 4 minutes for ~250 iterations.
"Cats having an auction.":

It's also interesting to see the development of details over iterations.
"Dragon flying over Aberystwyth tiltshift":

I'm really looking forward to exploring this use of GANS more to see how far it can go. It's easy to see a world where these images can be generated in milliseconds, in much greater detail, where story telling can be highly interactive and immersive. Combined with the likes of GPT, you could have entirely dynamic games with dialogue and imagery generated in response to user input. The mind game from Ender's Game comes to mind.
DLT is frequently in the news for its applications to financial transactions, asset tracking and configuration management, etc. One are I think is overlooked is the application in artificial intelligence. An obvious application in the AI space is resource management and tracibility of data processing, something already explored in other domains. But what about blockchain as a mechanism for developing AI?
In a recent patent we explored the implementation of evolutionary algorithms utiilising blockchain as a form of immunological memory. In our trial application we used the technique to create a network that was resilient to emerging threats, allowing distributed nodes to learn from one another. I'm keen to see further developments in this manner, where individual agent experience can be used to improve the knowledge of a larger community.
I've been involved in a few pieces of research in the theme of side-channel attacks in the past year.
- T. Andrade, M. Smith-Creasey and J. F. Roscoe, "Discerning User Activity in Extended Reality Through Side-Channel Accelerometer Observations", 18th International Conference on Intelligence and Security Informatics (ISI), IEEE, 2020 (Best Presentation Award)
- J. F. Roscoe and M. Smith-Creasey, "Unconventional Mechanisms for Biometric Data Acquisition via Side-Channels", SIN '20: 13th International Conference on Security of Information and Networks, ACM, 2020
- J. F. Roscoe and M. Smith-Creasey, "Acoustic Emanation of Haptics as a Side-Channel for Gesture-Typing Attacks", International Conference on Cyber Security and Protection of Digital Services (Cyber Security), IEEE, 2020
It's always interesting when you can see technology being applied in ways you don't expect. When it's a security risk, the mitigation can often be challenging.
In the case of acoustic cryptanalysis of haptic feedback when gesture typing, we have surmised there are just a few mitigation options, which have been filed as patent PCT/EP2021/054386.
Data entry on computing devices such as smartphone, tablet, laptop or other devices can include the entry of secret, confidential, private or other sensitive information, Such data is susceptible to interception by third parties such as malicious parties during a data input process. Accordingly, it is desirable to provide protections against data interception during a data input process.
According to a first aspect of the present invention, there is provided a computer implemented method to protect data input to a user input device from detection, the device including an artificial haptic feedback mechanism arranged to generate an occurrence of haptic feedback for sensing by a user of the device in response to each input gesture on the device by the user, characterised in that at least a subset of each occurrence of haptic feedback is adjusted with respect to a previous occurrence of haptic feedback by one or more of: a timing of the haptic feedback with respect to a time of occurrence of a corresponding input gesture; an adjustment to a duration of haptic feedback relative to a duration of the previous occurrence of haptic feedback; and a generation of one or more addition occurrences of haptic feedback.
With traditional haptics, security requires a tradeoff with usefulness, though there are no doubt alternative approaches that will be revealed over time.
Other approaches have involved the use of white noise or targetted noise cancelling hardware.

I'm pleased to be appearing as a cyber security panellist for STEMtastic21, the second virtual Science, Technology, Engineering and Maths (STEM) event from West Suffolk College, which is being supported by BT amongst others.
8th – 12th March 2021
Adastral Park, home of Applied Research, places a huge focus on the next generation of technologists – hosting around 8,000 school children each year, offering a free programme of stimulating events, virtual learning resources and working with global universities, to bring exciting careers in STEM to life. From 8th-12th March, BT is bringing Virtual British Science week to schools, pupils and parents!
- Monday 8th March - Cyber Security
- Tuesday 9th March - Smart Cities
- Wednesday 10th March - Creative Media
- Thursday 11th March - Drones
- Friday 12th March - Health & Sports Science
For more details, or to register, visit the Adastral Park website: https://atadastral.co.uk/bsw/

Our paper received the Best Presentation award at the 18th Annual IEEE International Conference on Intelligence and Security Informatics.

Very happy to receive this along with my colleagues Max and Tiago. 2020 was a challenging year for all in many ways. The transition of most conferences to an online only format made it much easier to submit and attend in greater numbers, but there's definitely a challenge to presenting over video. It's great to hear that our presentation was selected as being outstanding amongst all of the other excellent and engaging talks.
Pleased to announce that I have been appointed chair of the IEEE UK & Ireland Cyber Security Group. A newly formed group that aims to provide a multidisciplinary environment for sharing the latest trends and knowledge across industry, government and academia. Members are a diverse set of experts, bringing together insights into the technological, psychological and economic challenges faced in information security.
The proliferation of digital services in the modern world means that cyber security has profound and significant consequences for both organisations and individuals. The threat landscape has changed drastically over the years and continues to do so, demanding future preparedness and ongoing personal development for cyber security professionals.
We seek to provide evidence-based understanding of future security and privacy, to guide industry in effective and reliable implementation of security mechanisms as well as understanding the threats posed by emerging technologies and behaviour.
Chapter activities include webinars, workshops and networking events as well as sponsoring related activities. Please get in touch to volunteer or suggest new activities.

Really proud that our project Mobius was awarded the Excellence in Cyber Security award by the IET. It's great to have our work recognised and we were up against some great nominees.
Connected and autonomous vehicles (CAVs) are an emerging technology that will introduce new threats to the general public. Impending standards (such as ISO21434) demonstrate that there is a real cyber security risk and a need for supporting infrastructure in the form of vehicle security operations centre.
Mobius began in January 2020 as a combination of traffic simulation and web-based geospatial analytics. It was developed with the aim of enabling anomaly detection in a population of mixed manual, semi-autonomous and autonomous vehicles. The aim is to assist in identifying vehicles that may have become compromised as well as supporting planning and decision-making processes.
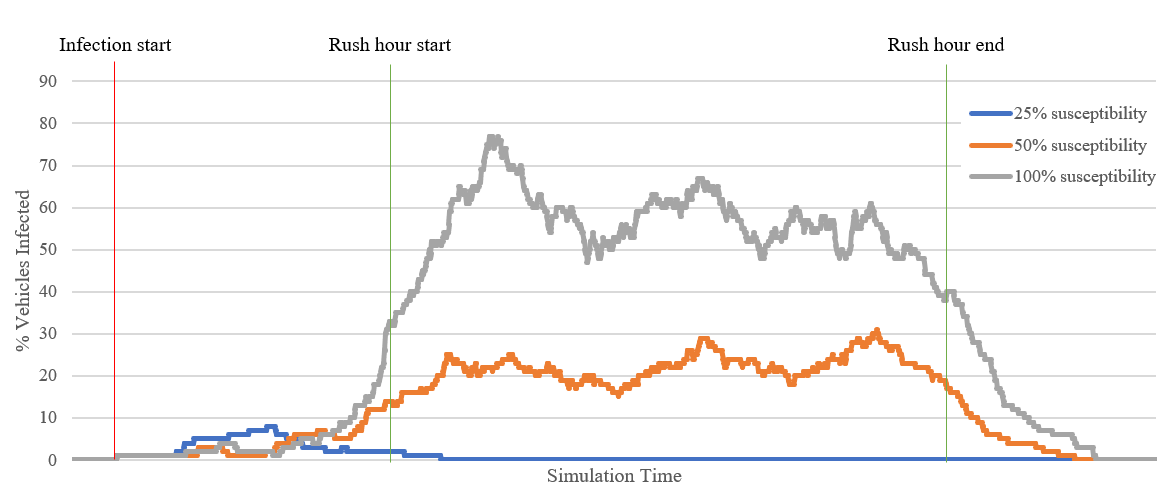
Mobius enables complex modelling of cyber physical traffic incidents using urban traffic data and vehicle information. The severity of malware incidents can be controlled through parameters, which simulate the impact of various types of malware. The spread of malware over V2X communications is modelled through traditional epidemiological models, incorporating the susceptibility of individual vehicles to infection and parametrically altering the rate of infection spread through traffic over a period of time.
As we migrate to future CAV systems, the number of computing and network components will dramatically increase. Both internal to vehicles, from vehicles to base stations and between vehicles on the road. The security envelope and attack surface is thus no longer restricted to the vehicles manufactured on-board systems. In this emerging CAV environment, we will see the spread of malicious code between vehicles, and base stations, in a similar manner to the spread of biological pathogens. Indeed, recent research at BT has demonstrated how simulations using such models can help accurately predict the spread of malware across large-scale computing networks.

Described as "frightening" in peer review, this new paper is a first step in identifying the landscape of potentially undocumented biometric privacy concerns with modern technology.
Side-channels are a simply fascinating aspect of computer security, where the implementation of a system results in a means of subverting it, rather than a flaw in the design itself. A popular example is the acoustic side-channel where, by listening to a user on a keyboard, you can determine the keys being pressed, allowing you to eavesdrop on all their input.
Other examples include the use of mechanical hard drive heads as microphones and reversed polarity LEDs as single pixel image sensors.
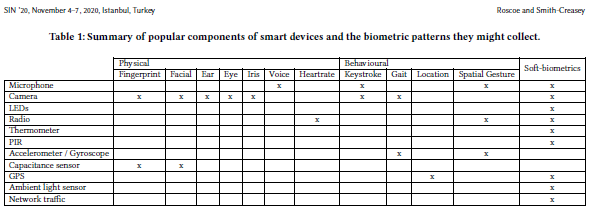
More and more devices are becoming ubiquitous and whilst many people are aware of the overt sensors and risks that may carry, they aren't aware of the ingenious way inconspicuous features of the technology might be used to acquire their biometric data.
This initial paper is a summary introduction to the potential side-channels proven in literature to be capable of collecitng biometric data.
It will be presented in November at the ACM SIN '20 conference.
Our concept paper for IEEE ISI conference was accepted and will be presented next month.
It's very early work that we aim to develop thoroughly over the coming months, but highlights an important issue for those seeking to utilise XR (virtual reality, mixed reality, etc.) for secure applications.
Whilst a lot of public attention is on the gaming aspect of XR, there is an increasing population of enterprise users. This makes security of those working in XR paramount.
In our experimentation we found that a simple wearable acceleromter (such as found in a smart watch or phone) is sufficient to differentiate between different activities (in this case Half Life: Alyx, Beat Saber or Pistol Whip).
With sufficient training data we anticipate that it will be feasible to identify specific actions carried out my a user (such as entering credentials, or interacting with applications in a specific way) which would enable eavesdropping on a user in VR.

BT's Mobius, our tool for simulating malware epidemiology in vehicles has been shortlisted for the IET's innovation annual awards.
Mobius is designed for use in security operations centres for local authorities, manufacturers and security services to identify anomalies in vehicle behaviour and model the impact malware might have in the real world.
Traffic simulation is a valuable tool in understanding the impact of increasingly autonomous levels of road use. For local authorities, fleet management and other organisations deploying vehicle security operations there will be major challenges in dealing with CAVs as they interact with the real world.
Application of compartmental models for epidemiology were implemented, allowing for propagation of malware between vehicles and infrastructure to be modelled. With a larger population, malware can persist for longer and potentially cause reinfections and have a larger impact, even with a relatively low rate of infection. Simulations will allow for an assessment of effectiveness that technological diversity presents as a barrier to malware transmission and the spread of its effect, directly through the spread of malware from vehicle to vehicle.
Geospatial analytics will play a crucial role in analysing the behaviour of vehicles and detecting anomalous behaviour when intelligence from intra-vehicle IDS may not be sufficient. As new standards that necessitate establish security operation centres, there is an increasing need for robust technology to understand vehicle behaviour.
Two new patents published today that work together to support the configuration and discovery of distributed sequential transactional databases (aka distributed ledger technology, or blockchain).
CONFIGURING DISTRIBUTED SEQUENTIAL TRANSACTIONAL DATABASES
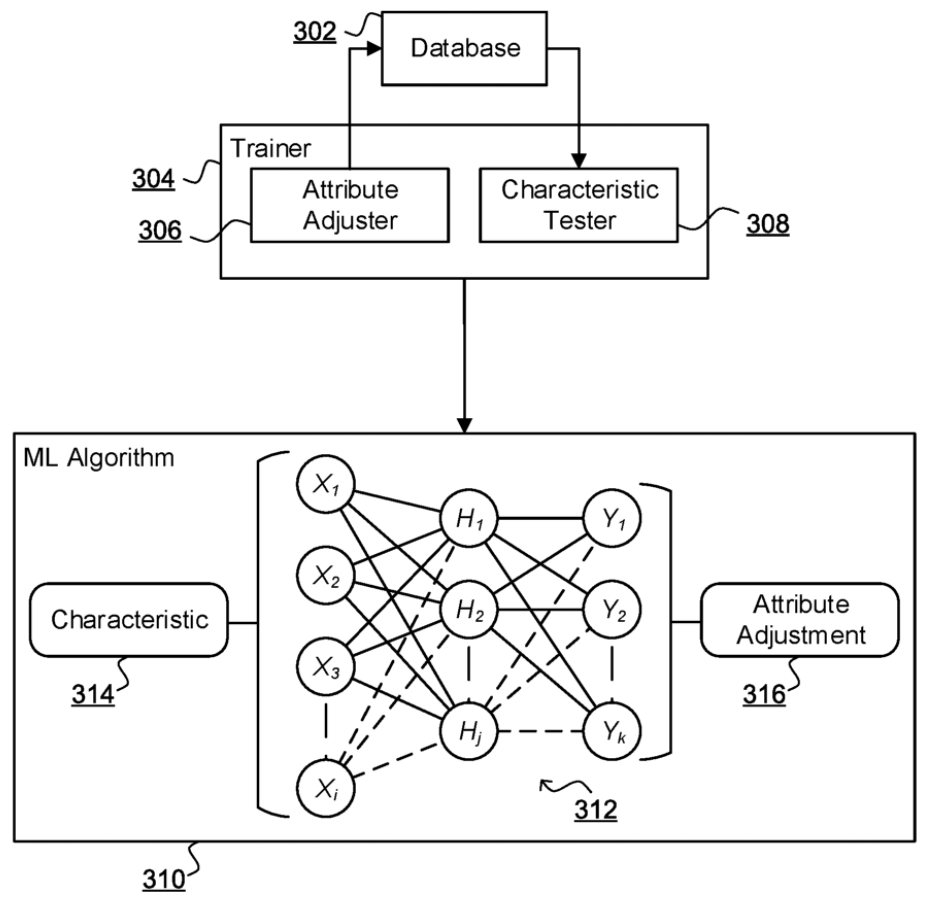
Distributed ledgers are living breathing ecosystems, subject to change based on behaviour of participants. The first invention provides a mechanism for DLT users to specificy a minimum acceptable configuration, almost like a service level agreement. Intelligent mechanisms help maintain blockchain homeostasis by managing the provisioning of resources to adjust performance. It's not suitable for public or proof-of-work based ledgers, but ideal for private ones where minimum levels of performance must be guaranteed.
A computer implemented method of configuring a distributed sequential transactional database for a software application operating with the database, the method comprising: receiving a descriptor for the application specifying characteristics of the database required for the application; accessing the databases to determine an extent to which each the database complies with the characteristics in the descriptor; responsive to the determination, identifying one or more attributes of the database for adjustment based on the characteristics in the descriptor so as to improve the extent of compliance of the database with the characteristics in the descriptor, the one or more attributes being determined by a machine learning algorithm trained to categorise database characteristics in terms of suitable adjustments; adjusting the database in accordance with the determined attributes.
DISTRIBUTED SEQUENTIAL TRANSACTIONAL DATABASE SELECTION
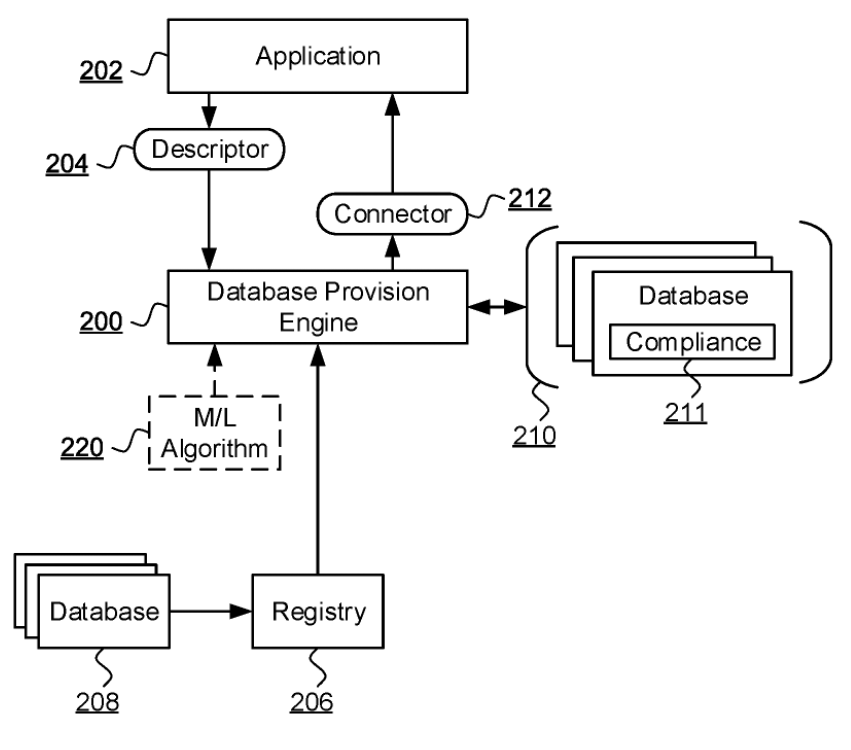
The second invention aims to simplify and promote DLT usage through the use of an intelligent discovery system. Rather than tying an application to a single blockchain, you specify the requrements for your application and a suitable one is found. You can even have trade offs, for example, an IoT application may favour guarantuee of delivery rather than security, whilst the opposite might be true of a financial application. This also means an application can make use of muiltiple blockchains over its lifetime.
A computer implemented method of provisioning a distributed sequential transactional database for a software application comprising: receiving a descriptor for the application specifying characteristics of the database required for the application; accessing a registry of distributed sequential transactional databases and filtering the registry based on the descriptor to define a subset of databases; accessing each of at least some of the databases in the subset to verify an extent to which each accessed database complies with the characteristics in the descriptor, and associating a degree of compliance with each accessed database, such that databases in a subset of accessed databases having a degree of compliance meeting a threshold degree of compliance are determined to be compliant databases; ranking the compliant databases in terms of the degree of compliance to select a database for access by the application.
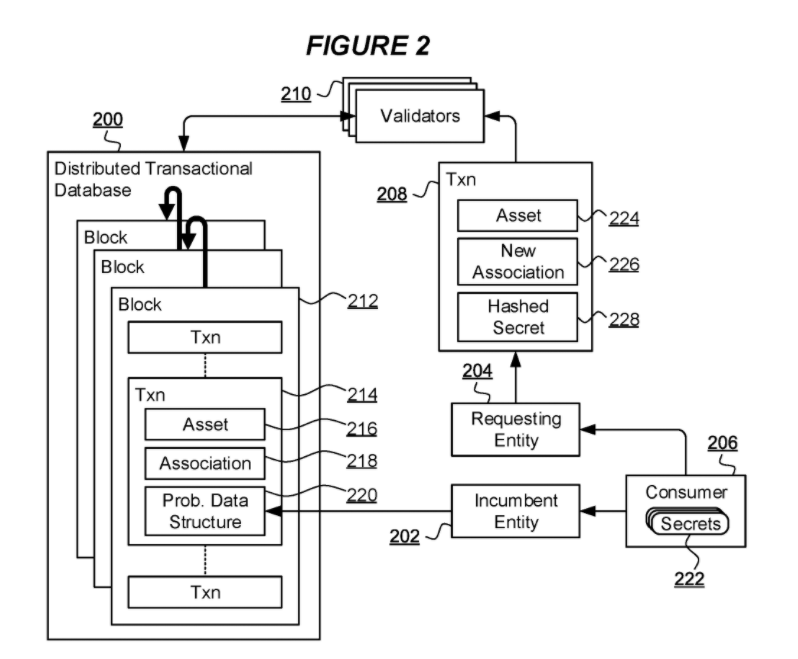
A computer implemented method of shared secret validation for a transaction to transfer an association of a digital asset represented in a distributed transactional database from an incumbent entity to a requesting entity, the asset having associated a probabilistic data structure encoding at least one digital hash of each of a plurality of secrets including the shared secret, and the transaction including a hash of the shared secret, the method comprising: validating the transaction by comparing the hash of the shared secret in the transaction with the probabilistic data structure; and responsive to the validation, committing the transaction in the database to effect the transfer of association of the digital asset to the requesting entity.
One of the major challenges of blockchain technology is in ensuring privacy whilst allowing information to be independently verified. Zero knowledge proofs (wonderfully explained with the story of Ali Baba) is a great mechanism for a prover to demonstrate knowledge of a secret to a verifier, without giving away the secret itself.
But what about a scenario where two parties supposedly share a common secret and wish to prove that, whilst enabling a third-party to verify. For example, a blockchain-based central numbering database might use subscriber information as a form of authentication (i.e. replacing PAC - portable authentication code). Obviously, subscriber information is extremely sensitive and must be protected.
We developed an approach using bloom filters, a form of probabilistic data store. This allows the two parties to demonstrate that they both possess secret information (i.e. matching subscriber details) and allow a third-party to confirm that the same source information is being used, by comparing the two bloom filters.
In contrast, Figure 5b illustrates a Bloom filter generated to represent a hashed secret that is not consistent with those secrets encoded in the Bloom filter of Figure 4. The data item of Figure 5b nonetheless indicates bit positions having bits set that are set in the Bloom filter of Figure 4. Thus, validators 210 can conclude that the hashed secret of Figure 5b is consistent with data encoded in the Bloom filter of Figure 4 and a transaction including such hashed secret would be committed to the database 200. While inspection and comparison of the Bloom filter of Figure 4 and the hashed data item of Figure 5b leads to such a conclusion, the incumbent entity 202 itself is able to determine that the representation of the hashed secret of Figure 5b cannot be based on a real secret 222 of the consumer 206 because each bit set in the representation of Figure 5b corresponds to a different secret in the Bloom filter of Figure 4. Thus, while the validators commit a transaction on the basis of hashed data of Figure 5b, the incumbent entity 202 identifies a failure of validation and determines that the transaction 208 of the requesting entity 204 is invalid. In this case, the incumbent entity 202 can issue a new transaction specifically reversing the committed transaction 208 of the requesting entity 204 to reverse the transfer of association of the digital asset 216 such that the digital asset is re-associated with the incumbent entity 202.
The published patent can be seen on patentscope.

I'll be presenting at Blockchain Expo in November, which will be syndicated with IoT Tech and Artificial Intelligence expos:
Blockchain and Enterprise Cyber Security
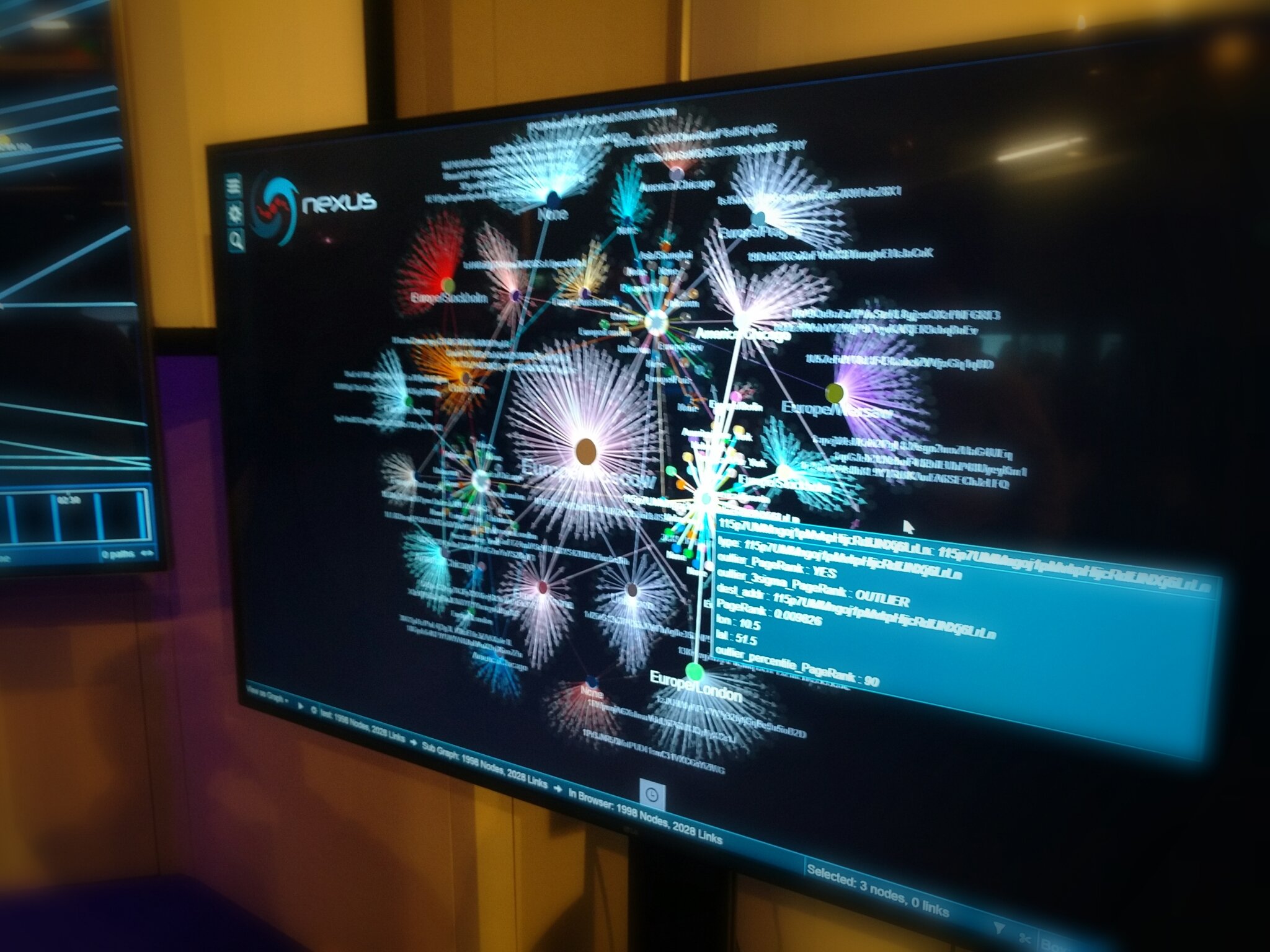
We explore some of the challenges present in the secure application of blockchain technology. With examples from the cryptocurrency Bitcoin, we present the pairing of new visualisation tools with machine learning in performing both forensic investigation and continuous monitoring of blockchain infrastructure.
This work is based upon practical application of prototype technology to real-world incidents. Initially supporting cybercrime investigators with new forensic tools, BT looks to apply its research to the increasing use of enterprise blockchains.
I’ll explore some of the challenges present in the secure application of blockchain technology. With examples from Bitcoin, I’ll present the pairing of new visualisation tools with machine learning in performing both forensic investigation and day-to-day health monitoring.
The bitcoin analytics work BT has carried out can be applied to many forms of blockchain technology and will be valuable with the rise in enterprise blockchains being deployed across industries for financial, access control and data management tasks. BT is continually developing its visual analytics and machine learning capabilities, applying the latest research to real cases.
Today I'll be presenting a paper on the use of compartmental epedmiological models for connected and autonomous vehicles at the IEEE International Conference on Computing, Electronics & Communications Engineering.

The most well-known SIR model assumes immunity following infection and transmission decreases as the pool of susceptible individuals is reduced.
It's a short pilot study as part of the ResiCAV project. Our main takeaway is that technological diversity will be crucial in preventing pervasive malware attacks in a population of vehicles. This sounds obvious, but it's an issue previously seen in other areas such as cash machine (ATM), where the reuse of standard components and design patterns eases deployment but means that a handful of attacks are applicable to a broad variety of machines (see ATM logic attacks).
Abstract
Connected and autonomous vehicles (CAVs) are an emerging technology that will introduce new threats to the general public. Impending standards (such as ISO21434) demonstrate that there is a real cyber security risk and a need for supporting infrastructure in the form of vehicle security operations centre.
In this concept paper we discuss some of the issues facing vehicle security as the technology matures over the next few years and look at how epidemiological models for malware might be developed to address concerns over vehicle cyber threats.
We detail our development of Mobius, a bespoke tool for simulating and analysing malware events in CAVs and explore how the technology might be applied to support real-world decision making.
As a part of the need for cyber resilience, we suggest there is a key role for vehicle simulation software capable of modelling cyber threats to assist with threat analysis and decision making for highway authorities, OEMs and fleet operators, amongst others. We present a summary of compartmental epidemiological models and the role they can play in understanding malware propagation for CAVs.
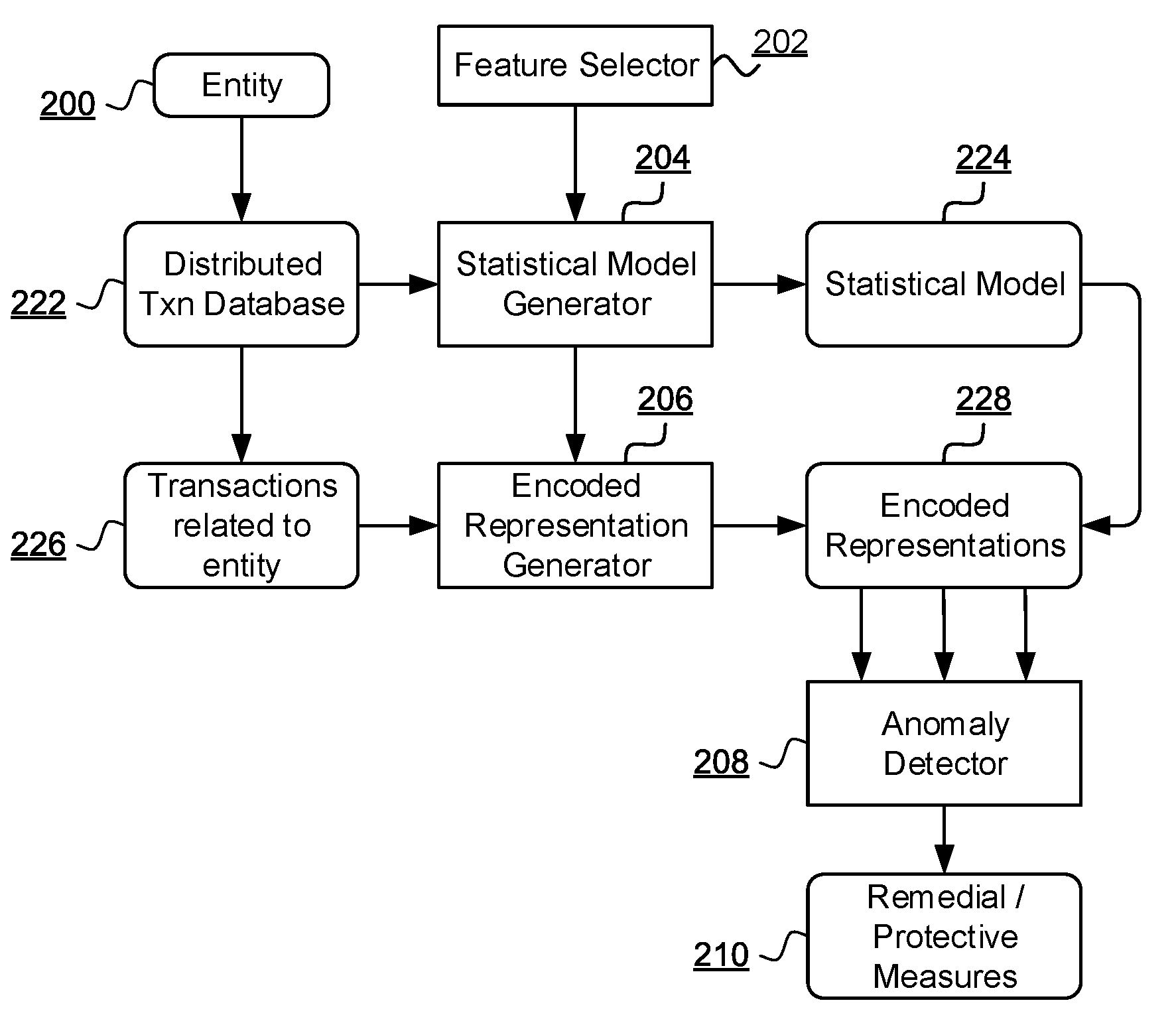
New patent publication that seeks to cover techniques we developed for categorising different actors on a blockchain using vectors built from neighbourhood characteristics.
A computer implemented method of anomalous behaviour detection of an entity transacting in a distributed transactional database, the method comprising: selecting a subset of features of at least a first subset of transactions in the database as a feature set; generating a statistical model of the first subset of transactions in terms of the selected features; identifying a second subset of transactions in the database comprising transactions related to the entity; generating an encoded representation of each transaction in the second subset based on a comparison of the selected features of the transaction with the statistical model, such that the encoded representation of at least some of the transactions in the second subset identify behaviour of the entity as anomalous.
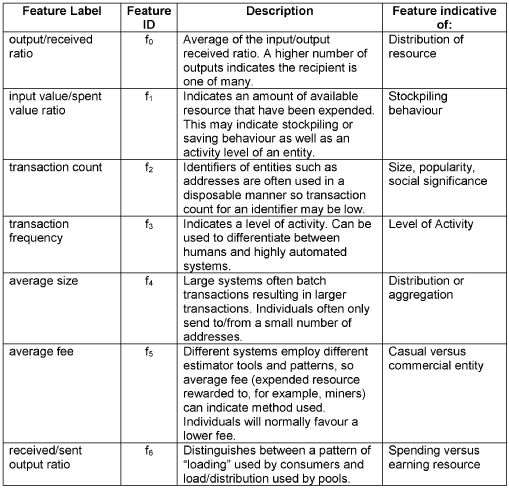
The table below defines, by way of example only, an ordered feature set in which earlier features are prioritised as more significant. An exemplary description of each feature and a suggestion of what each feature might indicate is also provided:
Full publication on WIPO: WO2020144021
New publication: Acoustic Emanation of Haptics as a Side-Channel for Gesture-Typing Attacks
In this paper, we show that analysis of acoustic emanations recorded from haptic feedback during gesture-typing sessions is a viable side-channel for carrying out eavesdropping attacks against mobile devices. The proposed approach relies on acoustic emanation resulting from haptic events, namely the buzz of a small vibration motor as the finger initiates the gesture-typing of a work in a sentence. By analysing time between haptic feedback events, it is possible to identify the text that a user enters via the soft keyboard on their device. The attack requires no prior interaction or need to install software on the target device (unlike similar works); only the ability to record audio within the vicinity. We present an experimental framework to illustrate the feasibility of the attack. In the experiments we show that sentences can be detected with an accuracy of 70% with some sentences identified with up to 95% accuracy. The attack can be conducted with minimal computation and on non-specialist consumer equipment. The paper concludes by proposing a number of countermeasures that mitigate the ability of an attacker to successfully intercept keyboard input.

Mobius is a malware simulation and propagation tool for connected and autonomous vehicles has been shortlisted for Best AI Product in Cyber Security at CogX 2020.
We developed Mobius at BT as part of the ResiCAV project to explore cyber security needs for future vehicles.

Shortly after the spread of coronavirus in the UK, Adastral Park became the headquarters for coimmunity face shield product, serving the East Suffolk & North Essex (ESNE) NHS trust and beyond.
I decided to get involved after hearing about rural healthcare workers lacking PPE. At first I was distributing shields in small quantity across the country through facebook using the two hobbyist 3D printers I have for building drones and cosplay props. But when I learned about the project at Adastral and the significant shortages going on locally I worked on increasing output and producing hundreds each week.

I was pleased to lead BT's work package for the recent ResiCAV project. The project highlights the need for the UK to establish key cyber security facilities as connected and autonomous vehicles (CAVs) TRLs continue to come closer.
ResiCAV – delivered by a consortium comprising HORIBA MIRA, Thales, BT, WMG at the University of Warwick, the Centre for Modelling & Simulation (CFMS), Oxfordshire County Council, AESIN Techworks, plus the University of South Wales, the University of Bristol, Coventry University and the National Digital Exploitation Centre (NDEC) – explored the feasibility of creating a UK Cybersecurity ‘Centre of Excellence’ to detect, understand and respond to emerging cybersecurity threats in real time across the mobility eco-system. The three-month programme was supported by funding from The Centre for Connected and Autonomous Vehicles (CCAV) and was run by Zenzic and Innovate UK.
“Ultimately, ResiCAV’s findings have highlighted the absolute and urgent need for a collaborative, industry-led, government-backed cybersecurity programme, hence our next steps will be to secure funding for the development of the ‘UK Centre of Excellence for Road Transport Cybersecurity Resilience’. Developing a world-class cybersecurity capability of this nature will be critical in building trust in CAV technologies as they are deployed, supporting the integration of CAV technologies across the UK’s future transport network.
Read the Horiba Mira news article
As part of the work, BT explored the threats and risks within intra- and inter-vehicular vehicle networks. We developed a bespoke traffic simulation tool incorporating compartmental models of epidemiology to observe the impact that malware can have on a population of vehicles.

Blockchains have received a lot of media hype recently. But what are they? Do I want one? This presentation will provide a basic understanding of the technology and its implementation challenges. We discuss the huge potential blockchains offer for more secure and reliable systems, but also consider the new threats that may emerge.
Cryptocurrencies saw an unprecedented surge in 2017 and the use of Bitcoin in cybercrime is an unaddressed and ongoing issue. Using real-world scenarios, we demonstrate the new tools being developed to help fight new threats.
This webinar will focus on the significance of blockchain from an enterprise perspective.
Firstly, we will explore ongoing research within the telecoms industry to build a blockchain for number management. This will demonstrate some of the key characteristics of good blockchain applications and the challenges faced in implementing.
Secondly, we will explore the security concerns around blockchain including homeostasis of private ecosystems as well as the impact of cryptocurrencies for business. We demonstrate the use of novel techniques in the forensic investigation of dark web sales.
We conclude with a look at the future opportunities for distributed ledger technology for enterprise and the steps needed to ensure the reliability of future systems.
This webinar is intended for everyone with an interest in blockchain technology. An understanding of blockchain would be useful but is not required.
Interview from NCSC workshop on safety v security at Southampton University.

Amid golden fields and disused military sites on the outskirts of the quiet town of Ipswich lies BT's version of the Google campus: Adastral Park.
It’s a grittier version of Silicon Valley, with fewer glass buildings and far more character. The telecoms giant has owned this 100-acre site for more than 40 years, when it was still called the Post Office Research Centre.
Principal researcher Jonathan Roscoe and his team at BT Applied Research are, among other things, using BT’s AI technology to monitor the bitcoin transactions which are available on the internet after a ransomware attack. “It’s about using AI to find suspicious activities in a number of wallets, and then we use that with the law enforcement agencies to link it to individuals who are behind these attacks,” he explains.
Article in the local paper on the work we're doing at Adastral Park.
Although, slight error, in the following paragraph they mix me up with my colleague Tiago Andrade, an expert in extended reality:
Mr Roscoe is a gamer, and was recruited because of his skills in that area.
 Presenting the virtual security operation centre (VSOC) at WIREDSmarter today.
Presenting the virtual security operation centre (VSOC) at WIREDSmarter today.

For my work in cryptocurrency analysis I was awarded ITP Innovator of the Year Winner 2018, sponsored by Nokia.

This was awarded for our work on forensic analysis of cryptoassets.
Enjoyed chatting about my research at #DSCS2017. Some great speakers and demos.
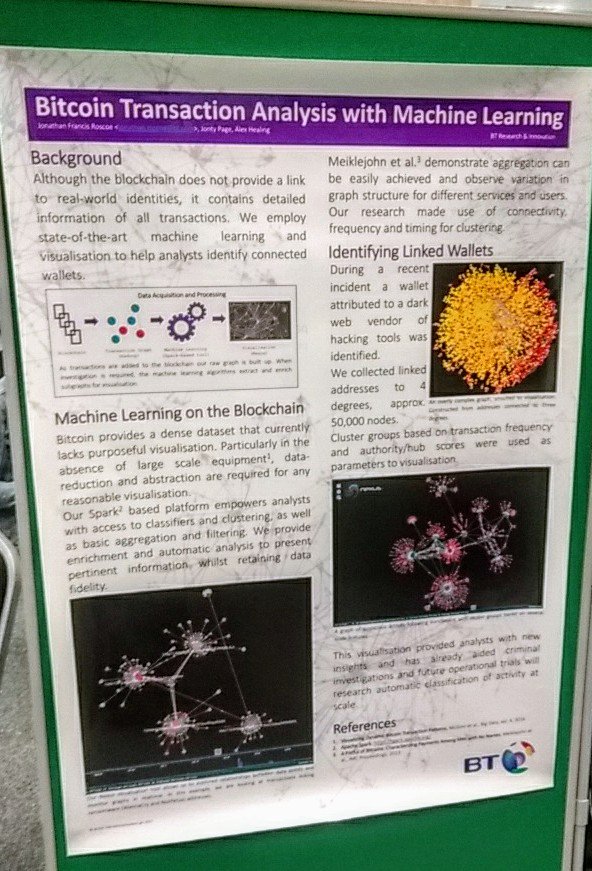
At BT's Innovation 2017, presenting some analytics research monitoring the bitcoin network for WannaCry ransomware payments.