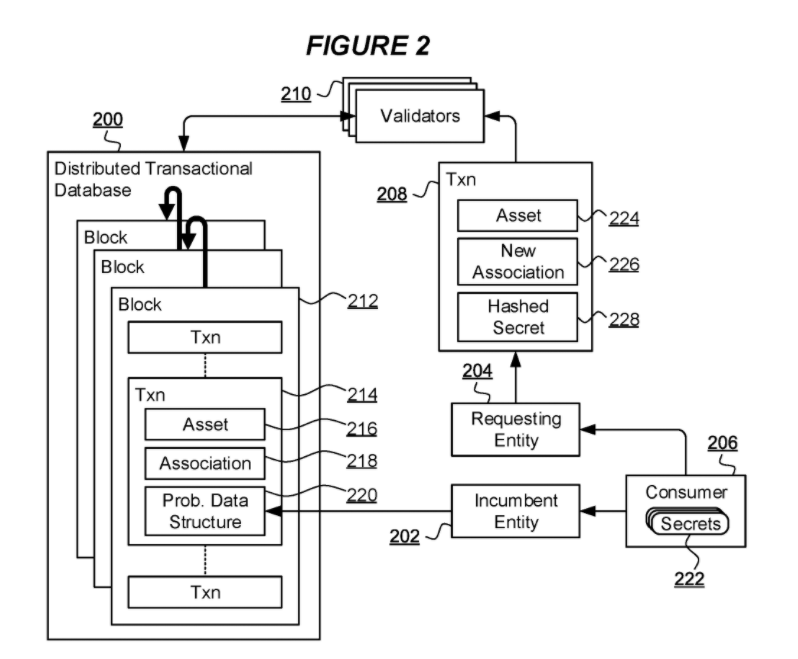
A computer implemented method of shared secret validation for a transaction to transfer an association of a digital asset represented in a distributed transactional database from an incumbent entity to a requesting entity, the asset having associated a probabilistic data structure encoding at least one digital hash of each of a plurality of secrets including the shared secret, and the transaction including a hash of the shared secret, the method comprising: validating the transaction by comparing the hash of the shared secret in the transaction with the probabilistic data structure; and responsive to the validation, committing the transaction in the database to effect the transfer of association of the digital asset to the requesting entity.
One of the major challenges of blockchain technology is in ensuring privacy whilst allowing information to be independently verified. Zero knowledge proofs (wonderfully explained with the story of Ali Baba) is a great mechanism for a prover to demonstrate knowledge of a secret to a verifier, without giving away the secret itself.
But what about a scenario where two parties supposedly share a common secret and wish to prove that, whilst enabling a third-party to verify. For example, a blockchain-based central numbering database might use subscriber information as a form of authentication (i.e. replacing PAC - portable authentication code). Obviously, subscriber information is extremely sensitive and must be protected.
We developed an approach using bloom filters, a form of probabilistic data store. This allows the two parties to demonstrate that they both possess secret information (i.e. matching subscriber details) and allow a third-party to confirm that the same source information is being used, by comparing the two bloom filters.
In contrast, Figure 5b illustrates a Bloom filter generated to represent a hashed secret that is not consistent with those secrets encoded in the Bloom filter of Figure 4. The data item of Figure 5b nonetheless indicates bit positions having bits set that are set in the Bloom filter of Figure 4. Thus, validators 210 can conclude that the hashed secret of Figure 5b is consistent with data encoded in the Bloom filter of Figure 4 and a transaction including such hashed secret would be committed to the database 200. While inspection and comparison of the Bloom filter of Figure 4 and the hashed data item of Figure 5b leads to such a conclusion, the incumbent entity 202 itself is able to determine that the representation of the hashed secret of Figure 5b cannot be based on a real secret 222 of the consumer 206 because each bit set in the representation of Figure 5b corresponds to a different secret in the Bloom filter of Figure 4. Thus, while the validators commit a transaction on the basis of hashed data of Figure 5b, the incumbent entity 202 identifies a failure of validation and determines that the transaction 208 of the requesting entity 204 is invalid. In this case, the incumbent entity 202 can issue a new transaction specifically reversing the committed transaction 208 of the requesting entity 204 to reverse the transfer of association of the digital asset 216 such that the digital asset is re-associated with the incumbent entity 202.
The published patent can be seen on patentscope.