Today I'll be presenting a paper on the use of compartmental epedmiological models for connected and autonomous vehicles at the IEEE International Conference on Computing, Electronics & Communications Engineering.

The most well-known SIR model assumes immunity following infection and transmission decreases as the pool of susceptible individuals is reduced.
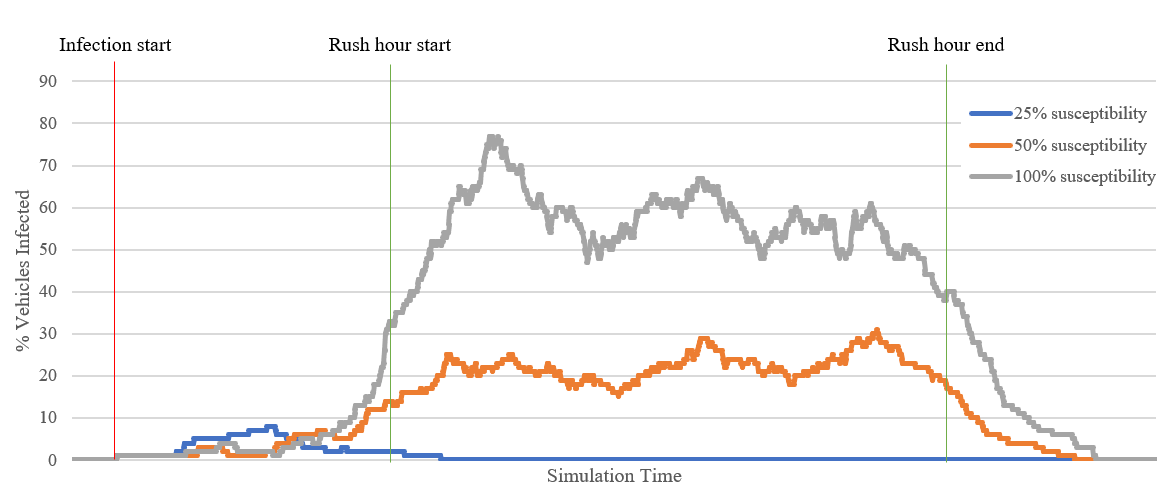
It's a short pilot study as part of the ResiCAV project. Our main takeaway is that technological diversity will be crucial in preventing pervasive malware attacks in a population of vehicles. This sounds obvious, but it's an issue previously seen in other areas such as cash machine (ATM), where the reuse of standard components and design patterns eases deployment but means that a handful of attacks are applicable to a broad variety of machines (see ATM logic attacks).
Abstract
Connected and autonomous vehicles (CAVs) are an emerging technology that will introduce new threats to the general public. Impending standards (such as ISO21434) demonstrate that there is a real cyber security risk and a need for supporting infrastructure in the form of vehicle security operations centre.
In this concept paper we discuss some of the issues facing vehicle security as the technology matures over the next few years and look at how epidemiological models for malware might be developed to address concerns over vehicle cyber threats.
We detail our development of Mobius, a bespoke tool for simulating and analysing malware events in CAVs and explore how the technology might be applied to support real-world decision making.
As a part of the need for cyber resilience, we suggest there is a key role for vehicle simulation software capable of modelling cyber threats to assist with threat analysis and decision making for highway authorities, OEMs and fleet operators, amongst others. We present a summary of compartmental epidemiological models and the role they can play in understanding malware propagation for CAVs.